PfSense
IPsec duble 2 phase (split connections)
(IKEv2 Only) When an IKEv2 tunnel has multiple Phase 2 definitions, by default the settings are collapsed in the IPsec configuration such that all P2 combinations are held in a single child SA.
Split Connections changes this behavior to be more like IKEv1 where each P2 is its configured by the daemon as own separate child SA.
Certain scenarios require this behavior, such as:
- The remote peer does not properly handle multiple addresses in single traffic selectors. This is especially common in Cisco equipment.
- Each child SA must have unique traffic selector or proposal settings. This could be due to the peer only allowing specific combinations of local/remote subnet pairs or different encryption options for each child SA.
Setting Up OpenVPN on PFSense 2.4.
Creating the Certificate Infrastructure needed for PFSense and OpenVPN
OpenVPN uses certificates to secure the VPN service for authentication and encryption purposes. The first thing we need to do on PFSense is create a Certificate Authority. If you already have one configured you can skip this step.
Creating a Certificate Authority on PFSense
The first step in the process is to navigate to the built-in PFSense Certificate Manager
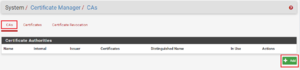
You will then be presented with a dashboard detailing the list of CA’s installed on the server. In the example below there isn’t one so click on +Add to create a new one.
Next we need to fill out the form which PFSense will use to create the Certificate Authority. Since we are building an Internal Certificate Authority, select this option from the drop-down list as highlighted in the image below and then fill out the necessary details about your organization in the fields provided. Remember to give you CA a useful common name which you can use to identify it. In my example I used PFSense_RootCA. Once done, click on Save and your Internal Certificate Authority will be created.