FreeIPA: различия между версиями
Перейти к навигации
Перейти к поиску
Sol (обсуждение | вклад) |
Sol (обсуждение | вклад) |
||
| (не показано 8 промежуточных версий этого же участника) | |||
| Строка 8: | Строка 8: | ||
== LE ssl certs == | == LE ssl certs == | ||
[https://github.com/freeipa/freeipa-letsencrypt с GitHUB] | [https://github.com/freeipa/freeipa-letsencrypt с GitHUB] | ||
| + | |||
| + | [https://www.freeipa.org/page/Using_3rd_part_certificates_for_HTTP/LDAP Оффициальный мануал] | ||
== FreeRadius == | == FreeRadius == | ||
| Строка 42: | Строка 44: | ||
openssl dhparam 2048 -out /etc/raddb/certs/dh | openssl dhparam 2048 -out /etc/raddb/certs/dh | ||
ipa-getcert request -w -k /etc/pki/tls/private/radius.key -f /etc/pki/tls/certs/radius.pem -T caIPAserviceCert -C 'systemctl restart radiusd.service' -N HOSTNAME -D HOSTNAME -K radius/HOSTNAME | ipa-getcert request -w -k /etc/pki/tls/private/radius.key -f /etc/pki/tls/certs/radius.pem -T caIPAserviceCert -C 'systemctl restart radiusd.service' -N HOSTNAME -D HOSTNAME -K radius/HOSTNAME | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | |||
| + | [http://firstyear.id.au/blog/html/2015/07/06/FreeIPA:_Giving_permissions_to_service_accounts..html Firstyear part1] [http://firstyear.id.au/blog/html/2016/01/13/FreeRADIUS:_Using_mschapv2_with_freeipa.html Firstyear part2] | ||
| + | |||
| + | [http://ilcofon.net/index.php/2018/01/05/wifi-authenticate-with-radius-and-freeipa/ Ilcofon Net] | ||
| + | |||
| + | |||
| + | == LDAP auth for Jira == | ||
| + | [https://www.freeipa.org/page/HowTos/LDAP_authentication_for_Atlassian_JIRA_using_FreeIPA FreeIPA DOC] | ||
| + | |||
| + | [https://confluence.atlassian.com/kb/how-to-write-ldap-search-filters-792496933.html How to write LDAP search filters] | ||
| + | |||
| + | [https://lists.fedorahosted.org/archives/list/[email protected]/thread/G2TK4XBMCE7QT6KPNN5ZE7RGMZJTZH2R Jira and Confluence user authentication with FreeIPA] | ||
| + | |||
| + | Протестированные и рабочие настройки | ||
| + | <syntaxhighlight lang="sql"> | ||
| + | mysql> select attribute_name, attribute_value from cwd_directory_attribute where directory_id ='10000'; | ||
| + | +----------------------------------------------------------------+--------------------------------------------------------------------------------------------------------------------------------------+ | ||
| + | | attribute_name | attribute_value | | ||
| + | +----------------------------------------------------------------+--------------------------------------------------------------------------------------------------------------------------------------+ | ||
| + | | autoAddGroups | | ||
| + | | com.atlassian.crowd.directory.sync.currentstartsynctime | NULL | ||
| + | | com.atlassian.crowd.directory.sync.issynchronising | false | ||
| + | | com.atlassian.crowd.directory.sync.lastdurationms | 373 | ||
| + | | com.atlassian.crowd.directory.sync.laststartsynctime | 1552648964065 | ||
| + | | crowd.sync.group.membership.after.successful.user.auth.enabled | only_when_first_created | ||
| + | | crowd.sync.incremental.enabled | true | ||
| + | | directory.cache.synchronise.interval | 3600 | ||
| + | | ldap.basedn | dc=local,dc=example,dc=ua | ||
| + | | ldap.connection.timeout | 10000 | ||
| + | | ldap.external.id | uid | ||
| + | | ldap.filter.expiredUsers | false | ||
| + | | ldap.group.description | description | ||
| + | | ldap.group.dn | cn=accounts | ||
| + | | ldap.group.filter | (&(objectclass=groupOfNames)(|(cn=jira-software-users)(cn=jira-administrators))) | ||
| + | | ldap.group.name | cn | ||
| + | | ldap.group.objectclass | groupOfNames | ||
| + | | ldap.group.usernames | Member | ||
| + | | ldap.local.groups | false | ||
| + | | ldap.nestedgroups.disabled | true | ||
| + | | ldap.pagedresults | false | ||
| + | | ldap.pagedresults.size | 1000 | ||
| + | | ldap.password | PASSWORD | ||
| + | | ldap.pool.initsize | NULL | ||
| + | | ldap.pool.maxsize | NULL | ||
| + | | ldap.pool.prefsize | NULL | ||
| + | | ldap.pool.timeout | 0 | ||
| + | | ldap.propogate.changes | false | ||
| + | | ldap.read.timeout | 120000 | ||
| + | | ldap.referral | false | ||
| + | | ldap.relaxed.dn.standardisation | true | ||
| + | | ldap.roles.disabled | true | ||
| + | | ldap.search.timelimit | 60000 | ||
| + | | ldap.secure | true | ||
| + | | ldap.url | ldaps://ipa1.local.example.ua:636 | ||
| + | | ldap.user.displayname | displayName | ldap.user.dn | cn=accounts | ||
| + | | ldap.user.email | mail | ||
| + | | ldap.user.encryption | sha | ||
| + | | ldap.user.filter | (&(objectclass=inetorgperson)(|(memberOf=cn=jira-software-users,cn=groups,cn=accounts,dc=local,dc=example,dc=ua)(memberOf=cn=jira-administrators,cn=groups,cn=accounts,dc=local,dc=example,dc=ua))) | | ||
| + | | ldap.user.firstname | givenName | ||
| + | | ldap.user.group | memberOf | ||
| + | | ldap.user.lastname | sn | ||
| + | | ldap.user.objectclass | inetorgperson | ||
| + | | ldap.user.password | userPassword | ldap.user.username | uid | ||
| + | | ldap.user.username.rdn | uid | ||
| + | | ldap.userdn | uid=USER,cn=users,cn=accounts,dc=local,dc=example,dc=ua | ||
| + | | ldap.usermembership.use | false | ldap.usermembership.use.for.groups | false | ||
| + | | localUserStatusEnabled | false +----------------------------------------------------------------+--------------------------------------------------------------------------------------------------------------------------------------+ | ||
| + | </syntaxhighlight> | ||
| + | |||
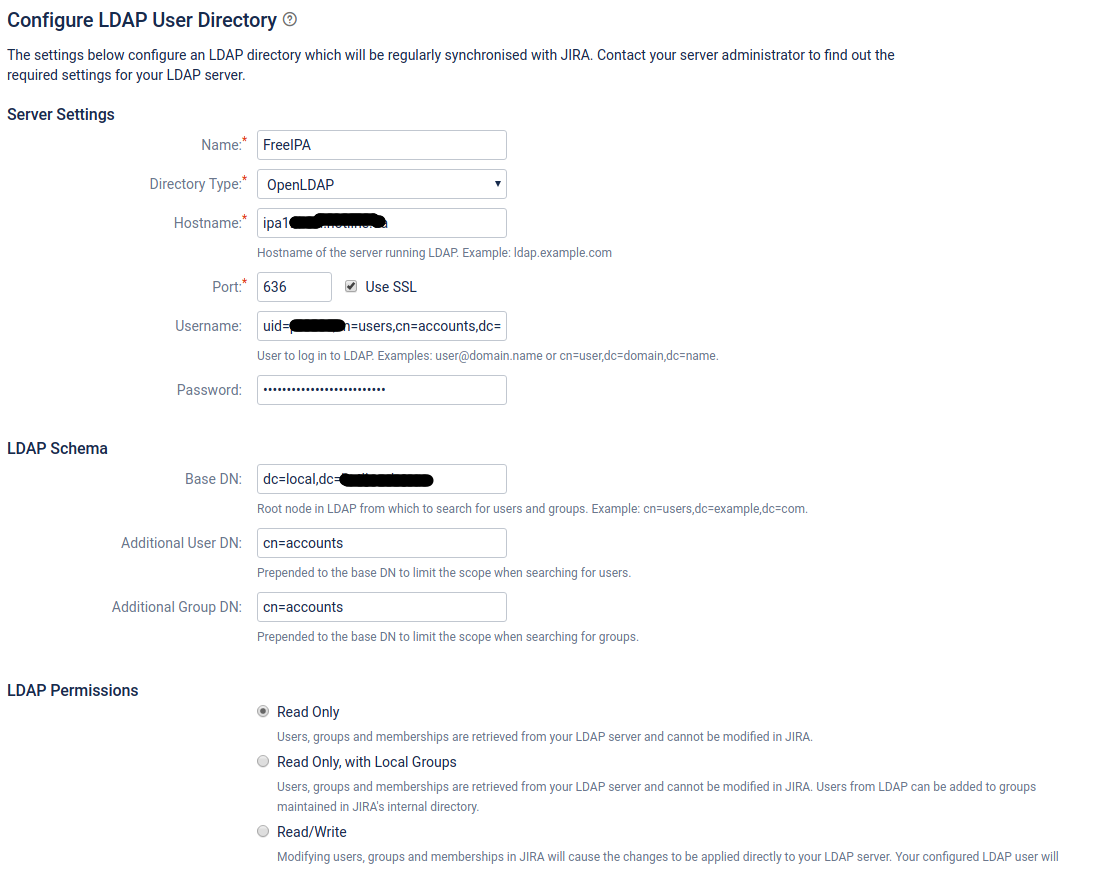
| + | [[Файл:2019-03-15 13-47-24.png|Configure LDAP User Directory:Server Settings,LDAP Schema,LDAP Permissions ]] | ||
| + | |||
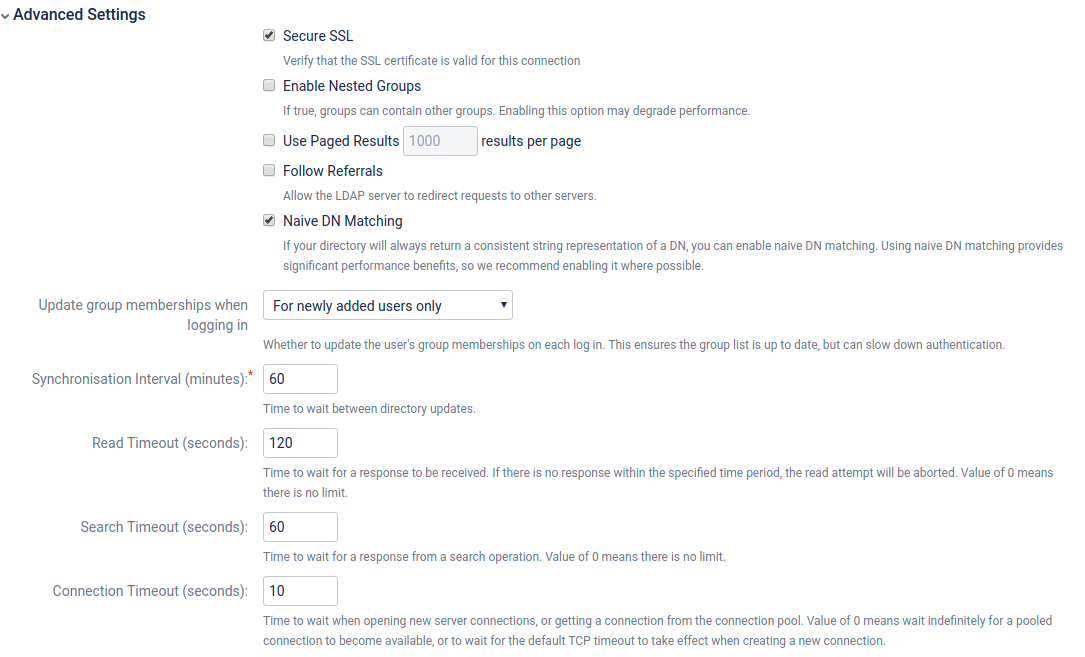
| + | [[Файл:2019-03-15 13-50-11.png|Configure LDAP User Directory:Advanced Settings]] | ||
| + | |||
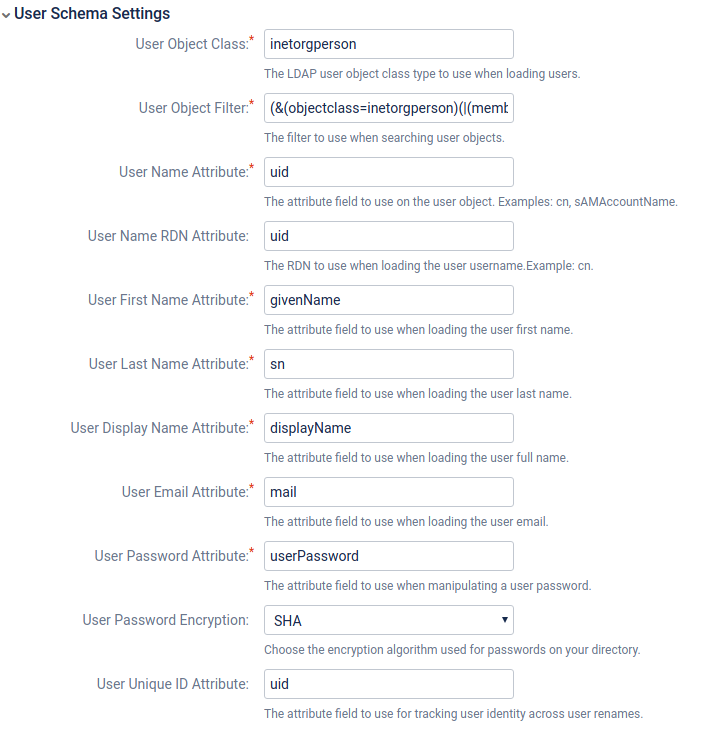
| + | [[Файл:2019-03-15 13-50-31.png|Configure LDAP User Directory:User Schema Settings]] | ||
| + | |||
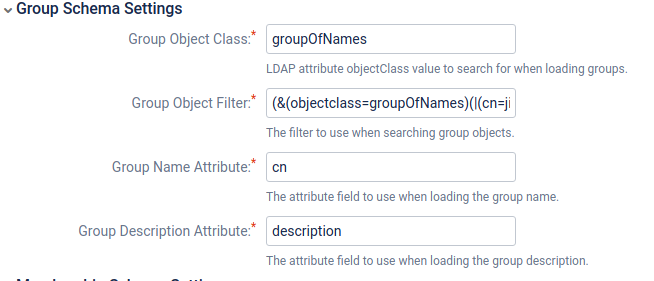
| + | [[Файл:2019-03-15 13-50-46.png|Configure LDAP User Directory:Group Schema Settings]] | ||
| + | |||
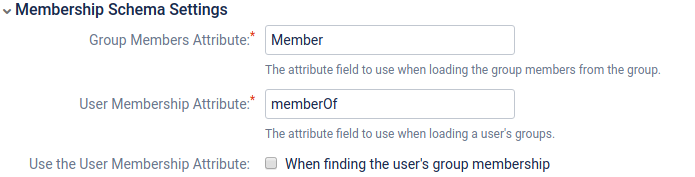
| + | [[Файл:2019-03-15 13-51-02.png|Configure LDAP User Directory:Membership Schema Settings]] | ||
| + | |||
| + | |||
| + | == LDAP auth for GitLab == | ||
| + | |||
| + | vim /etc/gitlab/gitlab.rb | ||
| + | <syntaxhighlight lang="bash"> | ||
| + | gitlab_rails['ldap_enabled'] = true | ||
| + | gitlab_rails['ldap_servers'] = YAML.load_file('/etc/gitlab/freeipa_settings.yml') | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | vim /etc/gitlab/freeipa_settings.yml | ||
| + | <syntaxhighlight lang="bash"> | ||
| + | main: | ||
| + | label: 'IPA' | ||
| + | host: 'ipa1.local.example.ua' | ||
| + | port: 389 | ||
| + | uid: 'uid' | ||
| + | method: 'tls' | ||
| + | bind_dn: 'uid=USER,cn=users,cn=accounts,dc=local,dc=example,dc=ua' | ||
| + | password: 'PASSWORD' | ||
| + | encryption: 'plain' | ||
| + | timeout: 10 | ||
| + | active_directory: false | ||
| + | allow_username_or_email_login: false | ||
| + | block_auto_created_users: false | ||
| + | verify_certificates: false | ||
| + | base: 'cn=users,cn=accounts,dc=local,dc=example,dc=ua' | ||
| + | user_filter: '(memberOf=cn=devs,cn=groups,cn=accounts,dc=local,dc=example,dc=ua)' | ||
| + | attributes: | ||
| + | username: ['uid'] | ||
| + | email: ['mail'] | ||
| + | name: 'displayName' | ||
| + | first_name: 'givenName' | ||
| + | last_name: 'sn' | ||
</syntaxhighlight> | </syntaxhighlight> | ||
Текущая версия на 14:05, 15 марта 2019
FreeIPA (Free Identity, Policy and Audit) — открытый проект для создания централизованной системы по управлению идентификацией пользователей, задания политик доступа и аудита для сетей на базе Linux и Unix. Развитие проекта осуществляется сообществом разработчиков при спонсорской поддержке Red Hat.
Установка
LE ssl certs
FreeRadius
# create keytab for radius user
ipa service-add 'radius/radius/HOSTNAME'
ipa-getkeytab -p 'radius/HOSTNAME' -k /etc/raddb/radius.keytab
chown root:radiusd /etc/raddb/radius.keytab
chmod 640 /etc/raddb/radius.keytab
# make radius use the keytab for SASL GSSAPI
mkdir -p /etc/systemd/system/radiusd.service.d
cat > /etc/systemd/system/radiusd.service.d/krb5_keytab.conf << EOF
[Service]
Environment=KRB5_CLIENT_KTNAME=/etc/raddb/radius.keytab
ExecStartPre=-/usr/bin/kdestroy -A
ExecStopPost=-/usr/bin/kdestroy -A
EOF
systemctl daemon-reload
edit /etc/raddb/mods-enabled/ldap
ldap server = 'LDAP HOSTNAME'
ldap base_dn = 'cn=accounts,dc=example,dc=org'
ldpa sasl mech = 'GSSAPI'
ldpa sasl realm = 'YOUR REALM'
ldap sasl update control:NT-Password := 'ipaNTHash'
# certs
mv /etc/raddb/certs /etc/raddb/certs.bak
mkdir /etc/raddb/certs
openssl dhparam 2048 -out /etc/raddb/certs/dh
ipa-getcert request -w -k /etc/pki/tls/private/radius.key -f /etc/pki/tls/certs/radius.pem -T caIPAserviceCert -C 'systemctl restart radiusd.service' -N HOSTNAME -D HOSTNAME -K radius/HOSTNAME
Firstyear part1 Firstyear part2
LDAP auth for Jira
How to write LDAP search filters
Jira and Confluence user authentication with FreeIPA
Протестированные и рабочие настройки
mysql> select attribute_name, attribute_value from cwd_directory_attribute where directory_id ='10000';
+----------------------------------------------------------------+--------------------------------------------------------------------------------------------------------------------------------------+
| attribute_name | attribute_value |
+----------------------------------------------------------------+--------------------------------------------------------------------------------------------------------------------------------------+
| autoAddGroups |
| com.atlassian.crowd.directory.sync.currentstartsynctime | NULL
| com.atlassian.crowd.directory.sync.issynchronising | false
| com.atlassian.crowd.directory.sync.lastdurationms | 373
| com.atlassian.crowd.directory.sync.laststartsynctime | 1552648964065
| crowd.sync.group.membership.after.successful.user.auth.enabled | only_when_first_created
| crowd.sync.incremental.enabled | true
| directory.cache.synchronise.interval | 3600
| ldap.basedn | dc=local,dc=example,dc=ua
| ldap.connection.timeout | 10000
| ldap.external.id | uid
| ldap.filter.expiredUsers | false
| ldap.group.description | description
| ldap.group.dn | cn=accounts
| ldap.group.filter | (&(objectclass=groupOfNames)(|(cn=jira-software-users)(cn=jira-administrators)))
| ldap.group.name | cn
| ldap.group.objectclass | groupOfNames
| ldap.group.usernames | Member
| ldap.local.groups | false
| ldap.nestedgroups.disabled | true
| ldap.pagedresults | false
| ldap.pagedresults.size | 1000
| ldap.password | PASSWORD
| ldap.pool.initsize | NULL
| ldap.pool.maxsize | NULL
| ldap.pool.prefsize | NULL
| ldap.pool.timeout | 0
| ldap.propogate.changes | false
| ldap.read.timeout | 120000
| ldap.referral | false
| ldap.relaxed.dn.standardisation | true
| ldap.roles.disabled | true
| ldap.search.timelimit | 60000
| ldap.secure | true
| ldap.url | ldaps://ipa1.local.example.ua:636
| ldap.user.displayname | displayName | ldap.user.dn | cn=accounts
| ldap.user.email | mail
| ldap.user.encryption | sha
| ldap.user.filter | (&(objectclass=inetorgperson)(|(memberOf=cn=jira-software-users,cn=groups,cn=accounts,dc=local,dc=example,dc=ua)(memberOf=cn=jira-administrators,cn=groups,cn=accounts,dc=local,dc=example,dc=ua))) |
| ldap.user.firstname | givenName
| ldap.user.group | memberOf
| ldap.user.lastname | sn
| ldap.user.objectclass | inetorgperson
| ldap.user.password | userPassword | ldap.user.username | uid
| ldap.user.username.rdn | uid
| ldap.userdn | uid=USER,cn=users,cn=accounts,dc=local,dc=example,dc=ua
| ldap.usermembership.use | false | ldap.usermembership.use.for.groups | false
| localUserStatusEnabled | false +----------------------------------------------------------------+--------------------------------------------------------------------------------------------------------------------------------------+
LDAP auth for GitLab
vim /etc/gitlab/gitlab.rb
gitlab_rails['ldap_enabled'] = true
gitlab_rails['ldap_servers'] = YAML.load_file('/etc/gitlab/freeipa_settings.yml')
vim /etc/gitlab/freeipa_settings.yml
main:
label: 'IPA'
host: 'ipa1.local.example.ua'
port: 389
uid: 'uid'
method: 'tls'
bind_dn: 'uid=USER,cn=users,cn=accounts,dc=local,dc=example,dc=ua'
password: 'PASSWORD'
encryption: 'plain'
timeout: 10
active_directory: false
allow_username_or_email_login: false
block_auto_created_users: false
verify_certificates: false
base: 'cn=users,cn=accounts,dc=local,dc=example,dc=ua'
user_filter: '(memberOf=cn=devs,cn=groups,cn=accounts,dc=local,dc=example,dc=ua)'
attributes:
username: ['uid']
email: ['mail']
name: 'displayName'
first_name: 'givenName'
last_name: 'sn'